ETHICAL HACKING 101
A Complete Course To Become Zero To Professional Ethical Hacker
Duration
Self-paced
Timing
Flexible
Access
Lifetime
Completion
Certification
Who is this for?
- People who want to start their carrier in cybersecurity
- Who does not have any knowledge in cybersecurity
- Who want to make money finding bugs in weak systems
- Web developers who want to secure their websites
- Students who want to secure their systems
- Ethical Hackers who want to advance their skills
What You Will Learn
- All 5 stages of hacking
- How to setup lab and install Kali Linux with 3 victim machines
- How trojans, viruses and worms are created
- bypassing firewalls, ids and honeypots
- Cracking WIFI passwords
- Gaining access to windows, linux and android
- Making huge amount of money with bug bounty
- Disconnect anyone from WiFi network
- Gaining access to any router
- Networking Fundamentals & Advance topics
- Web Application Hacking
- SQL Injection, Cross Site Scripting
Prerequisites
- No Pre Knowledge Required
- A Computer or Laptop
95%
Practical
TRAINING MODULES

Introduction to Ethical Hacking Pentesting
A Detailed overview of ethical hacking Pentesting and its importance in cybersecurity.

Footprinting and Reconnaissance
Gathering information about a target system or network.

Scanning Networks
Techniques for discovering hosts and services on a network.
Enumeration
Gathering information about users, groups, shares, and services on a system.

Vulnerability Analysis
Identifying and assessing vulnerabilities in a system or network.

Python 101
Introduction to the Python programming language.

Python Scripting
Writing Python scripts to automate tasks and perform security-related tasks.

System Hacking
Latest Techniques for gaining unauthorized access to a system.

Malware Threats
Overview of malware types and how they can be used in attacks.

C++ Uncovered
Introduction to the C++ programming language & Creating Malware.

Sniffing
Techniques for intercepting and analyzing network traffic.

Social Engineering
Psychological techniques used to manipulate people into divulging sensitive information.

Denial-of-Service
Techniques for disrupting access to a system or network.

Session Hijacking
Techniques for taking over a user's session on a system or network.

Hacking Web Servers
Advance Techniques for attacking, Hacking & Securing web servers.
Hacking Web Applications
Advance Techniques for attacking. Hacking & Securing web applications.

PHP & Javascript
Introduction to PHP and JavaScript programming languages for understanding attacks better.

SQL Injection
Practical techniques used to exploit vulnerabilities in SQL databases.

Hacking Wireless Networks
Cracking the security protocols in a wireless network, granting full access for the hacker to view, store, download, or abuse the wireless network.

Hacking Mobile Platforms
Vulnerabilities found in mobile platforms such as Android and iOS, and provides practical guidance on how to exploit them.

Java Programming
An introduction to the Java programming language, How it can be used to understand mobile hacking better.

IoT & IoT Hacking
Covers the techniques used to attack Internet of Things devices and networks.

Cloud Computing
Overview of cloud computing technology and the security issues associated with it.

Cryptography
Provides an overview of encryption and decryption techniques.

CTFs
Introduces Capture the Flag competitions and techniques for solving challenges.

Freelancing
Covers the opportunities for freelancing in cybersecurity.

Earning On Fiverr
Key aspects of creating an effective gig, such as creating a compelling title and description, setting a competitive price, and providing high-quality work samples.
Bug Bounty
Discusses how to participate in bug bounty programs on HackerOne & BugCrowd.

Create Your Portfolio
Creating a portfolio from complete scratch and showcasing your skills.

Security Firm Registration (US Based)
The process for registering a security firm in the US & Offering Your Services.
Detailed Syllabus Overview
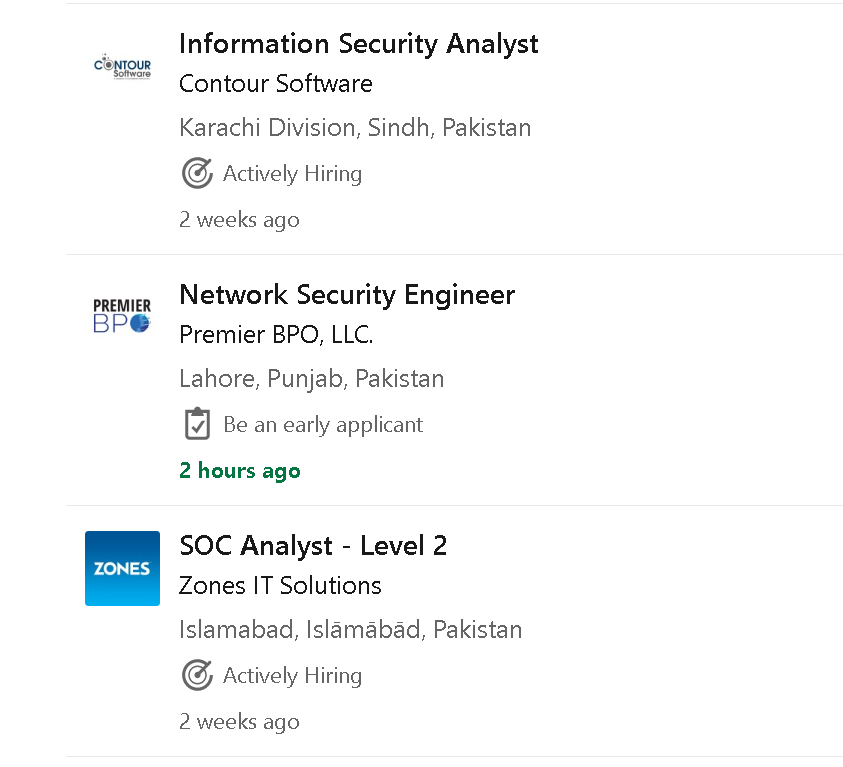
CyberSecurity Scope
Bug bounty programs offer monetary rewards to ethical hackers for successfully discovering and reporting a vulnerability or bug to the application's developer.






Considering the good salary, flexible work hours, and the option to work from home, most people are now preparing themselves for a career in cyber security.





Detailed Scope Overview
Certifications
Crack International Certifications To Get Job In Europe or US





Reviews
What others have to say about this course






Frequently Asked Questions
All of your quesrions answered at one place.
Your access to the content will be for LIFETIME.
You don’t need any prior knowledge for this training, since everything will start from the complete basics to advance level. We will start from “What os hardware?” “What is software”. Even if you are from a completely different field and want to pursue a career in cybersecurity, you will be able to do i easily.
Lectures will be provided in learning management system along with assignments, quizzes and real life projects. Your progress will be recorded in the learning management system.
You will be connected on WhatsApp with you instructor who will guide you until you complete your training.
Yes, you will be able to access classes whenever you want and you will lead this training according to your own schedule.
This training is designed for 2-5 months learning pace which means you can complete it in 2 months or even 5 months or even more. Since you are learning on your own pace, as much time as you will give, it will complete as soon. On Average it takes around 5 months to complete this training.
This is a highly practical training as 95% content of this training is Practical and hands on.
You will be able to earn and get a job very easily since most of the students get internships even after 2 months of joining this training But it will all depend on how you take this course. If you will study with all your heart then it will be very easy to start earning after this training.
You can pay fee to even mobile accounts like Easypaisa, Jazzcash or ebanks like Nayapay or Sadapay or you can even transfer funds to bank accounts through mobile accounts and ebanks. If you dont have anything you can easily visit any shop with account details to submit your fee.
Start Learning Today
“An investment in knowledge pays the best interest”
OFFER EXPIRES IN
- 00Days
- 00Hours
- 00Minutes
- 00Seconds
PKR 30,000
PKR 10,000
one time payment
Limited Seats Available
✅ All tolls and softwares will b provided
✅ Kali Linux and Other 30 OS Will be Provided
✅ Lifetime Access to Sessions
✅ WhatsApp support for all the queries
✅ 2-5 Months Training
✅ 30+ Modules
✅ 50+ Projects and Assignments
✅ 1000+ Quizzes
✅ 150+ Hours of Content
✅ Real Live Attacks
✅ 1 on 1 Training
✅ Flexible timing
OR
PKR 15,000
PKR 5,000
2 Installments
Order At Checkout Page WIll Be Created Of Full Fee But Installment Can Be Paid
✅ All tolls and softwares will b provided
✅ Kali Linux and Other 30 OS Will be Provided
✅ Lifetime Access to Sessions
✅ WhatsApp support for all the queries
✅ 2-5 Months Training
✅ 30+ Modules
✅ 50+ Projects and Assignments
✅ 1000+ Quizzes
✅ 150+ Hours of Content
✅ Real Live Attacks
✅ 1 on 1 Training
✅ Flexible timing